Bypassing CORS and the Same-Origin Policy
Cross-Origin Resource Sharing (CORS) is a technique based on HTTP headers that limits the origins (outside the target domain) allowed to load resources on the client's side. Setting specific domains, schemes, or ports permitted to serve resources guarantees that clients can't be tricked into sharing sensitive data with third-party actors. Most modern-day applications strictly set a list of external origins that are allowed to bypass CORS.
With Fiddler Everywhere, you can easily create a rule that bypasses the pre-set CORS policies by overwriting the sent/received values with wildcards (or other specific values).
Creating a "Bypass CORS" Rule
This example shows how to create a rule named "Bypass CORS" that effectively sets the CORS policy not to a same-origin or specific domain but to all domains using a wildcard. This effectively bypasses the same-origin policy, which might allow third-party actors to execute a cross-site request forgery (CSRF). The rule should only be used for testing purposes where and when needed, not for real-life scenarios.
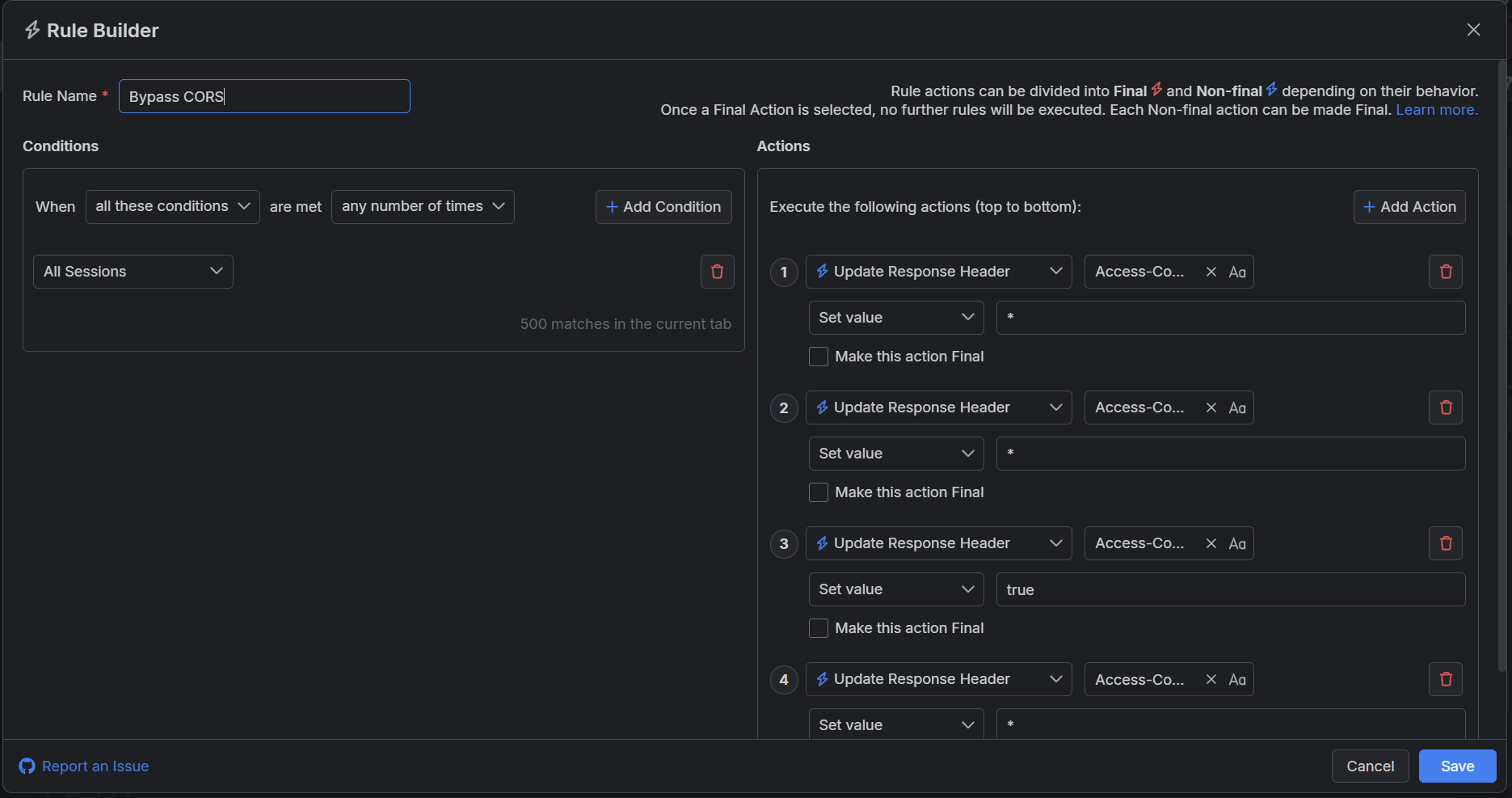
Create a "Bypass CORS" rule that sets the following actions through the Rules Builder.
- Create an action that sets the HTTP Response header Access-Control-Allow-Origin with a wildcard value
*. - Create an action that sets the HTTP Response header Access-Control-Allow-Methods with a wildcard value
*. - Create an action that sets the HTTP Response header Access-Control-Allow-Credentials with a boolean value
true. - Create an action that sets the HTTP Response header Access-Control-Allow-Headers with a wildcard value
*.
This sample Fiddler rule matches all sessions and bypasses the pre-set CORS policies.
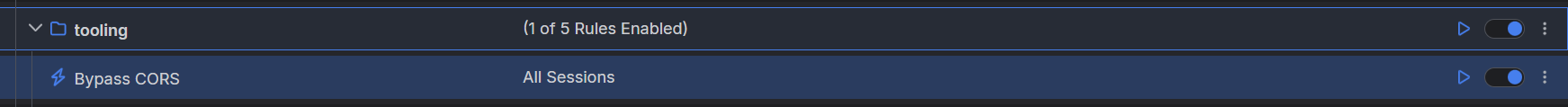
Once the rule is created, enable the Rules tab, toggle the rule switch, and start capturing traffic.
Download a ready-to-use "Bypass CORS" rule as a FARX file, which you can import through the Rules toolbar.